Microsoft Defender for Endpoint
This guide provides an objective overview of Microsoft Defender for Endpoint, detailing its capabilities, key features, deployment options, and benefits.
Beyond a conference — NerdioCon 2026: Learning, networking & unforgettable moments.
Save your spot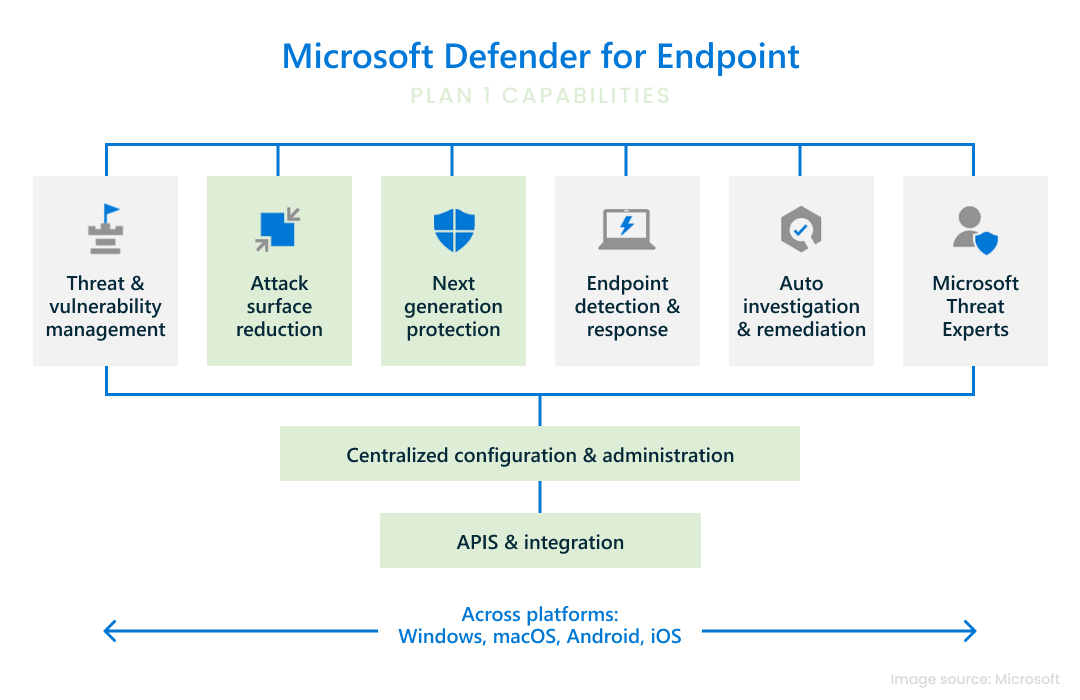
This guide provides an objective overview of Microsoft Defender for Endpoint, detailing its capabilities, key features, deployment options, and benefits.
Amol Dalvi | May 5, 2025
Microsoft Defender for Endpoint is a unified endpoint security platform, designed to help protect your organization from a wide range of cyberthreats. It goes beyond traditional antivirus solutions, providing you with advanced threat protection, endpoint detection and response (EDR), and vulnerability management.
By leveraging cloud-based security intelligence, machine learning, and artificial intelligence, Defender for Endpoint helps you proactively detect, investigate, and respond to threats targeting your devices, such as laptops, desktops, and servers. This comprehensive platform defends against malware, ransomware, phishing, and other cyber risks while consolidating your endpoint security tools into one solution. With a complete view of your organization’s security, it empowers you to strengthen defenses, reduce the risk of breaches, and minimize the impact of cyberattacks.
Microsoft Defender for Endpoint operates as a comprehensive security platform, combining advanced technologies to protect your organization’s devices from cyber threats. It integrates seamlessly with your existing IT infrastructure, offering real-time threat detection, prevention, and response capabilities.
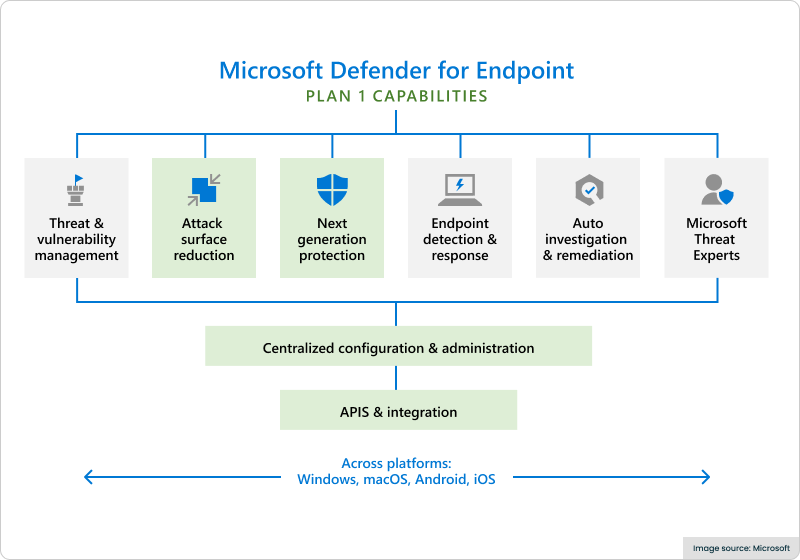
Let’s walk through the diagram above.
And, supporting all of these features,
| Category | Benefits for IT teams | Benefits for business leaders |
|---|---|---|
| Centralized management | Simplifies management of endpoint security across devices. | Provides a unified view of organizational security status. |
| Time efficiency | Reduces manual effort with automated threat detection and response. | Frees resources to focus on strategic business priorities. |
| Enhanced visibility | Offers detailed insights into security threats and vulnerabilities. | Boosts confidence in maintaining regulatory compliance. |
| Risk reduction | Strengthens defenses against cyber threats, minimizing downtime. | Safeguards sensitive business data from breaches. |
| Cost effectiveness | Reduces costs associated with manual investigations and mitigation. | Helps avoid financial and reputational losses from attacks. |
Microsoft Defender for Endpoint offers flexible deployment options to suit your organization’s unique needs and infrastructure. Whether you’re managing a small team or a global enterprise, you can choose the method that best aligns with your IT environment and operational goals.
You can deploy Microsoft Defender for Endpoint using various methods, depending on your existing tools and infrastructure:
Before deploying Microsoft Defender for Endpoint, ensure your environment meets these requirements:
Onboarding devices is a critical step in the deployment process. Here are the supported methods:
Defender for Endpoint is available through several licensing options to suit different organizational needs. Plan 1 delivers foundational security features like next-generation antivirus and attack surface reduction. Plan 2 expands on this with advanced capabilities such as endpoint detection and response (EDR), automated remediation, and access to Microsoft Threat Experts. Additionally, Microsoft 365 E5 includes all Plan 2 features as part of a comprehensive suite of security and productivity tools.
Here’s a comparison table summarizing the features included in Microsoft Defender for Endpoint Plan 1, Plan 2, and Microsoft 365 E5:
Microsoft Defender for Endpoint employs a multi-layered approach to protect your organization from cyberattacks. By combining advanced threat detection, prevention, and response capabilities, it helps you stay ahead of evolving threats and safeguard your endpoints. This protection is crucial for all organizational assets, including modern endpoints like Windows 365 Cloud PCs, which empower users with a personalized Windows experience on any device.
To prevent cyberattacks, Microsoft Defender for Endpoint reduces potential vulnerabilities by enforcing security policies through attack surface reduction. These policies limit entry points for attackers, such as restricting applications or controlling network access. Defender for Endpoint also helps secure common remote access methods like RDP, which is vital for enabling remote work and VDI access, by applying specific controls and monitoring to prevent unauthorized entry or exploitation of these connections. Additionally, its next-generation protection employs AI and machine learning to identify and block malware, ransomware, and phishing threats in real time. It identifies and prevents access to apps considered unsafe, even if they don’t qualify as malware. It also includes robust web and network protection, which prevents access to malicious websites or low-reputation internet destinations, further reinforcing your defenses.
Detection capabilities are powered by behavioral analytics, which continuously monitor endpoint activities to identify suspicious patterns indicative of threats. The solution also employs endpoint detection and response (EDR) to analyze data from endpoints in real time, generating alerts and actionable insights for further investigation. Enhanced by Microsoft’s global threat intelligence, Defender for Endpoint identifies attacker tools, techniques, and methods, allowing for timely and accurate detection of potential breaches.
When a cyberattack occurs, it automates investigations and remediation processes to address threats efficiently. It isolates compromised devices to contain the threat and prevent lateral movement within your network. For more complex incidents, Defender provides support through Microsoft Threat Experts, offering expert analysis and targeted notifications to enhance your response efforts. Together, these capabilities minimize the impact of attacks while reducing the workload on your IT team.
| Feature | Plan 1 | Plan 2 | Microsoft 365 E5 |
|---|---|---|---|
| Next-generation protection | Included | Included | Included |
| Attack surface reduction | Included | Included | Included |
| Endpoint detection and response (EDR) | Not included | Included | Included |
| Threat and vulnerability management | Not included | Included | Included |
| Automated investigation and remediation | Not included | Included | Included |
| Microsoft Threat Experts | Not included | Included | Included |
| Centralized configuration and APIs | Included | Included | Included |
| Integration with Microsoft 365 Defender | Limited | Full integration | Full integration |
| Advanced hunting | Not included | Included | Included |
| Licensing | Standalone or included in Microsoft 365 E3 | Standalone or included in Microsoft 365 E5 | Included as part of Microsoft 365 E5, along with additional advanced security and compliance features. |
Microsoft Defender for Endpoint stands out in the crowded endpoint security market by offering a unified platform with advanced capabilities like AI-driven threat detection and seamless integration with the Microsoft ecosystem. Here we compare it to other solutions to help you understand its unique strengths and potential limitations.
Microsoft Defender for Endpoint differentiates itself through its deep integration with Microsoft 365 and Azure services, providing a unified security experience. This deep integration is particularly evident in its robust protection for Azure-native services like Azure VDI, which enables businesses to securely scale virtual desktop deployments with centralized management, ensuring a cohesive security posture across both physical and virtual endpoints. This comprehensive approach to VDI security also encompasses the protection of user profile solutions like FSLogix, which is critical for delivering a seamless and personalized user experience in pooled virtual desktop environments, by safeguarding these profiles against threats. By securing these virtual endpoints, Defender for Endpoint plays a vital role in protecting the overall VDI infrastructure—the complete set of hardware and software delivering virtual desktops—thereby ensuring that these centralized environments remain a secure and reliable way for users to access corporate resources.
Defender for Endpoint’s AI-driven threat detection and automated remediation streamline your security operations, reducing manual effort. And the inclusion of Microsoft Threat Experts adds a layer of proactive threat hunting and expert consultation, which many competitors lack. Defender for Endpoint offers cross-platform support for Windows, macOS, Linux, Android, and iOS, ensuring consistent protection across your organization’s devices. Moreover, it’s adept at securing various DaaS (Desktop as a Service) solutions, which provide businesses with flexible, scalable virtual desktop environments accessible from anywhere, by extending its advanced threat protection capabilities to these cloud-hosted endpoints. This comprehensive coverage across the end user computing spectrum solidifies Defender for Endpoint's role as a cornerstone of modern workplace security.
Here we compare popular endpoint security solutions:
| Feature | Microsoft Defender for Endpoint | CrowdStrike Falcon | Symantec Endpoint Security |
|---|---|---|---|
| Integration with Microsoft tools | Full integration with Microsoft 365 and Azure | Limited | None |
| AI-driven threat detection | Included | Included | Included |
| Automated remediation | Included | Included | Limited |
| Cross-platform support | Windows, macOS, Linux, Android, iOS | Windows, macOS, Linux, Android, iOS | Windows, macOS, Android |
| Threat hunting services | Microsoft Threat Experts | Falcon OverWatch | Not included |
| Pricing | Competitive, with flexible licensing | Premium pricing | Mid-range pricing |
While Microsoft Defender for Endpoint excels in integration and automation, it may require a Microsoft-centric IT environment to fully leverage its capabilities. Organizations using non-Microsoft tools might face challenges in achieving seamless integration. Additionally, advanced features like EDR and automated remediation are only available in higher-tier plans, which could impact cost considerations for smaller businesses.
Nerdio simplifies and optimizes your use of Microsoft Defender for Endpoint by providing tools and features tailored for enterprise environments. From streamlining deployment to enhancing vulnerability management, Nerdio ensures you get the most out of your endpoint security solution.
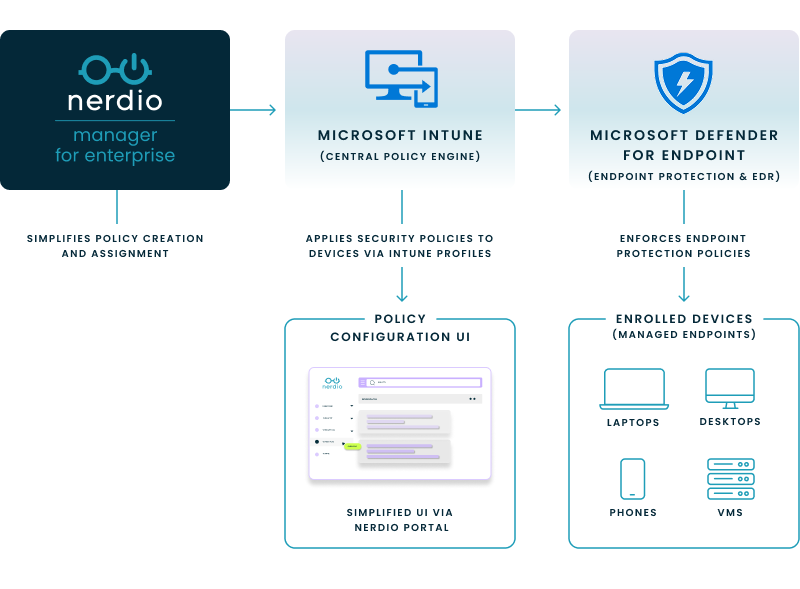
Nerdio enhances your experience by offering centralized management and automation tools that reduce administrative overhead. Nerdio simplifies the security and management of diverse endpoint landscapes, from physical devices to virtual desktops and Cloud PC instances, by ensuring consistent policy application and oversight through Microsoft Defender for Endpoint.
With Nerdio Manager, you can standardize Intune policies, ensuring consistent security configurations across your organization. It also provides a curated library of pre-built policies, enabling you to enforce security baselines and streamline policy deployment. Additionally, Nerdio’s integration capabilities allow you to manage Defender for Endpoint alongside other Microsoft tools, creating a unified and efficient security management experience.
Nerdio Manager provides a detailed, MSP-level overview of vulnerabilities detected by Microsoft Defender for Endpoint. You can search, sort, and filter vulnerabilities, as well as view details such as exposed devices and affected software. This granular visibility helps you prioritize and address vulnerabilities more effectively, reducing your organization’s risk exposure. By consolidating vulnerability data into a single interface, Nerdio simplifies the process of identifying and mitigating threats.
This comparison highlights how Nerdio complements Defender for Endpoint by simplifying management, accelerating deployment, and reducing administrative effort.
| Aspect | Using Defender for Endpoint alone | Using Defender for Endpoint with Nerdio |
|---|---|---|
| Deployment | Requires manual setup or use of native tools like Intune or MECM. | Simplifies deployment with pre-configured baselines and automated processes. |
| Policy management | Policies need to be manually created and maintained within Defender. | Provides a curated library of pre-built policies to streamline configuration. |
| Vulnerability management | Offers detailed insights and prioritization for vulnerabilities. | Enhances visibility with centralized MSP-level vulnerability views and filtering tools. |
| Onboarding devices | Relies on Defender's onboarding tools, which are effective but require setup. | Automates and accelerates onboarding with standardized processes. |
| Integration | Integrates well with Microsoft tools but requires separate configurations. | Unifies integration with Intune and other Microsoft tools into a cohesive workflow. |
| Scalability | Scalable but requires more manual effort for large or multi-tenant environments. | Easily scalable across complex environments with automation and multi-tenant support. |
| Administrative effort | Administrators manually manage deployment, policies, and vulnerability tasks. | Reduces administrative workload by automating repetitive tasks. |
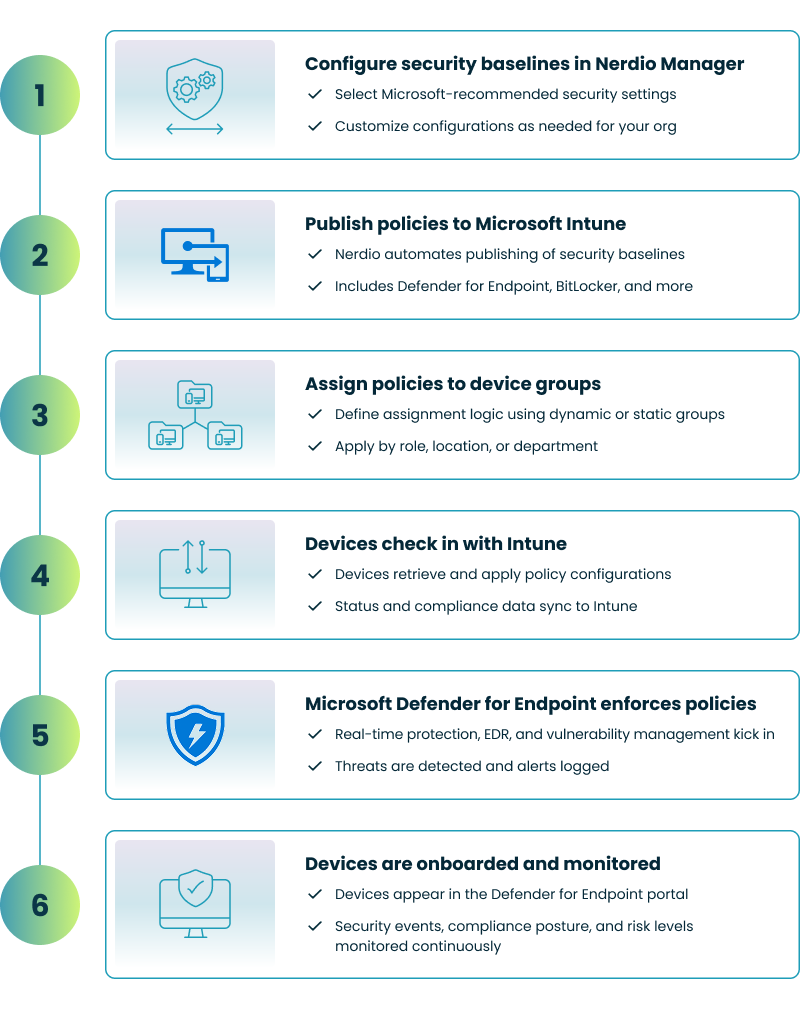
Nerdio accelerates deployment by offering pre-configured solution baselines for Microsoft Defender for Endpoint. These baselines include predefined settings and policies that align with best practices, reducing the time and effort required for setup. Nerdio also supports automated device onboarding, ensuring a smooth and consistent process across your organization. This is particularly valuable for enterprises managing large-scale or multi-tenant environments.
See this demo to discover how you can simplify operations, enhance security, and lower the total Azure cost of your entire Windows 365 or AVD environment with Nerdio Manager.
See how you can optimize processes, improve security, increase reliability, and save up to 70% on Microsoft Azure costs.
Getting started with Microsoft Defender for Endpoint involves a few key steps to ensure a smooth deployment and effective use of its features. By following a structured approach, you can quickly onboard devices, configure security settings, and begin protecting your organization from cyber threats.
Before deploying, ensure your environment meets these requirements:
Deployment methods vary based on your organization’s infrastructure and tools:
Here are the four main ways to onboard devices:
Once deployment is complete, you can:
Defender for Endpoint is an enterprise-grade security platform offering advanced features like endpoint detection and response (EDR), threat and vulnerability management, and automated remediation. Defender for Windows, often referred to as Windows Security or Microsoft Defender Antivirus, is the built-in antivirus solution for individual Windows devices, providing basic malware protection.
Microsoft Defender provides robust protection against malware, phishing, and other threats, especially when paired with advanced features in Defender for Endpoint. While it can suffice for many users, organizations with specific security needs or requirements may choose to use additional security tools for layered protection.
Defender for Endpoint focuses on securing devices like desktops, laptops, and servers from cyber threats. Defender for Office 365, on the other hand, protects your organization’s email and collaboration tools (e.g., Exchange Online, Teams, SharePoint) from threats such as phishing, spam, and malicious links or attachments.



Software product executive and Head of Product at Nerdio, with 15+ years leading engineering teams and 9+ years growing a successful software startup to 20+ employees. A 3x startup founder and angel investor, with deep expertise in Microsoft full stack development, cloud, and SaaS. Patent holder, Certified Scrum Master, and agile product leader.