Azure Load Balancer
This guide provides an objective overview of Azure Load Balancer, exploring different types, key features, use cases, pricing, and comparisons.
Beyond a conference — NerdioCon 2026: Learning, networking & unforgettable moments.
Save your spot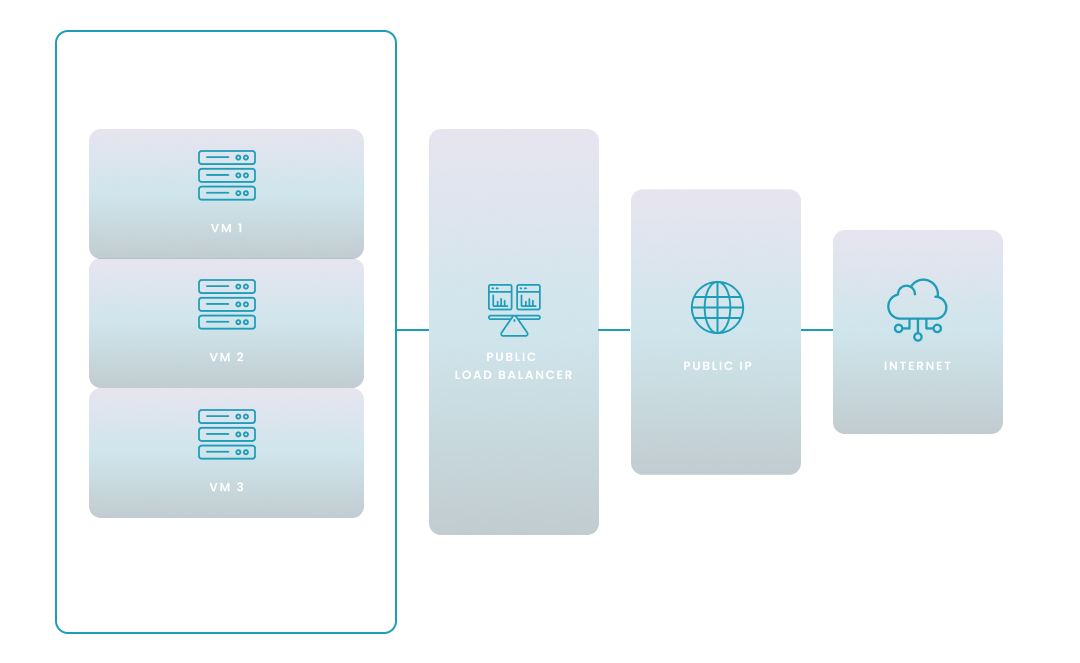
This guide provides an objective overview of Azure Load Balancer, exploring different types, key features, use cases, pricing, and comparisons.
Amol Dalvi | May 2, 2025
Azure Load Balancer is a core Microsoft Azure cloud service that distributes network traffic across multiple resources to ensure application availability, scalability, and performance. It's key to building resilient, scalable applications, distributing incoming traffic across backend resources like VMs, containers, or scale sets to prevent overload and maintain responsiveness.
This is critical for meeting your users’ expectations for high availability, as traffic spikes can overwhelm single servers. Load Balancer prevents this and eliminates single points of failure, rerouting traffic to healthy resources if a server fails.
Azure Load Balancer's operation at Layer 4 (Transport Layer) of the OSI model is fundamental to its versatility. This placement allows it to work with both TCP and UDP protocols, crucial for handling diverse network traffic. TCP, the connection-oriented protocol, is used for applications needing guaranteed delivery and order, like web browsing and file transfer. UDP, the connectionless protocol, prioritizes speed over reliability, serving applications like video streaming and online gaming.
By operating at Layer 4, Azure Load Balancer can distribute both TCP and UDP traffic, making it suitable for a wide range of applications and workloads, as we see below with the four types of load balancers available.
1. Public Load Balancer
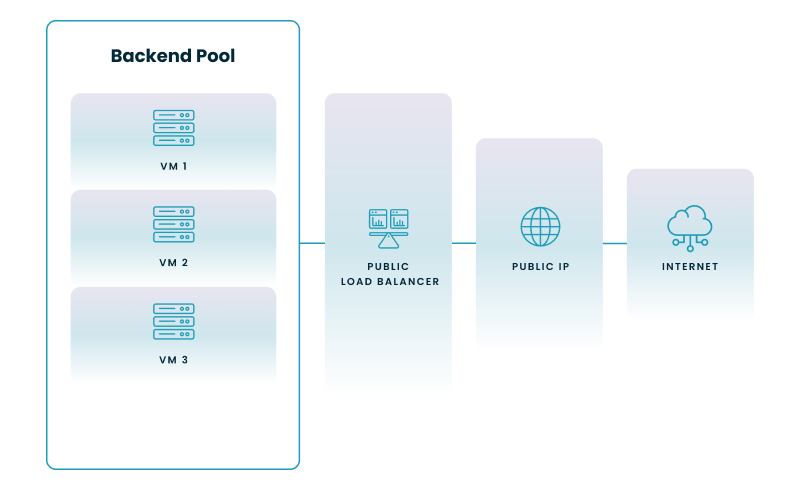
A Public Load Balancer connects your application to the internet. It distributes incoming internet traffic to your backend resources.
2. Internal Load Balancer
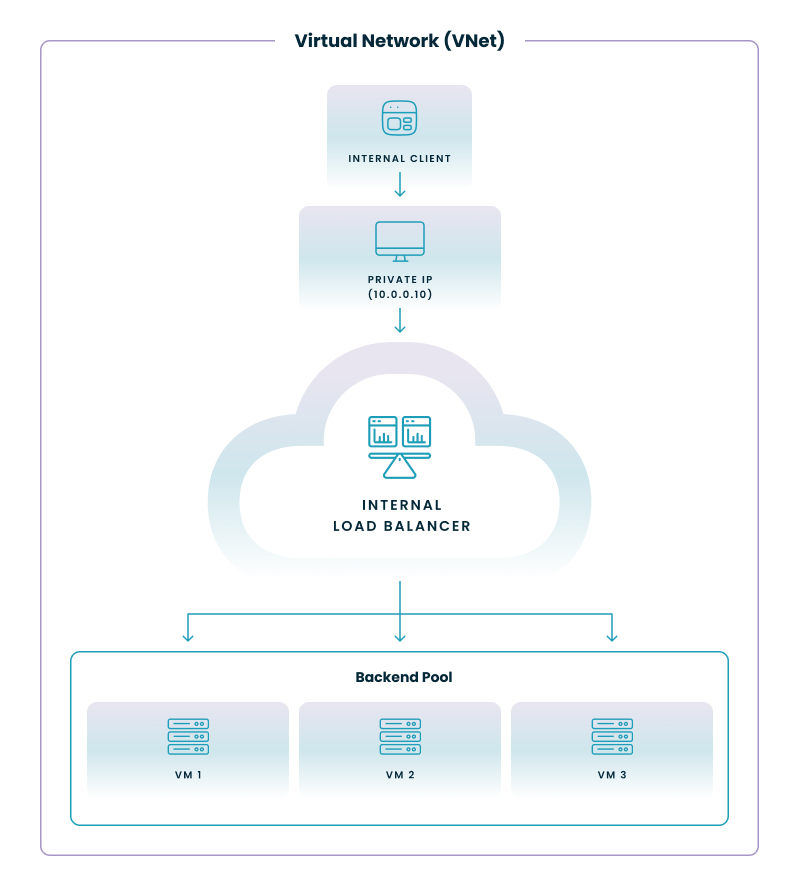
An Internal Load Balancer distributes traffic within your virtual network (VNet) or between VNets. It uses a private IP address and isn't accessible from the internet.
3. Application Gateway
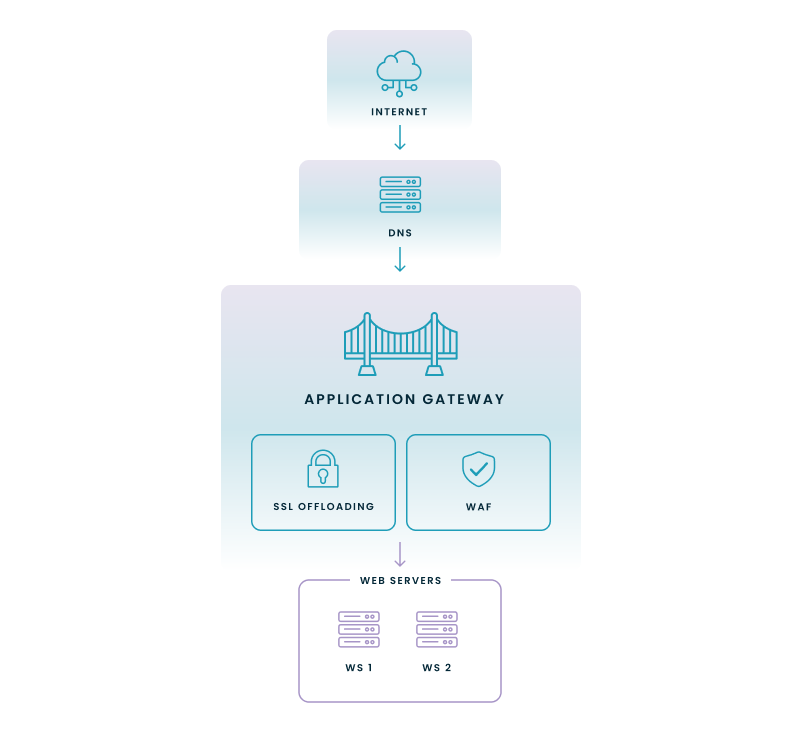
Application Gateway is a specialized load balancer for web applications. It operates at Layer 7 (application layer) and offers advanced features.
4. Traffic Manager
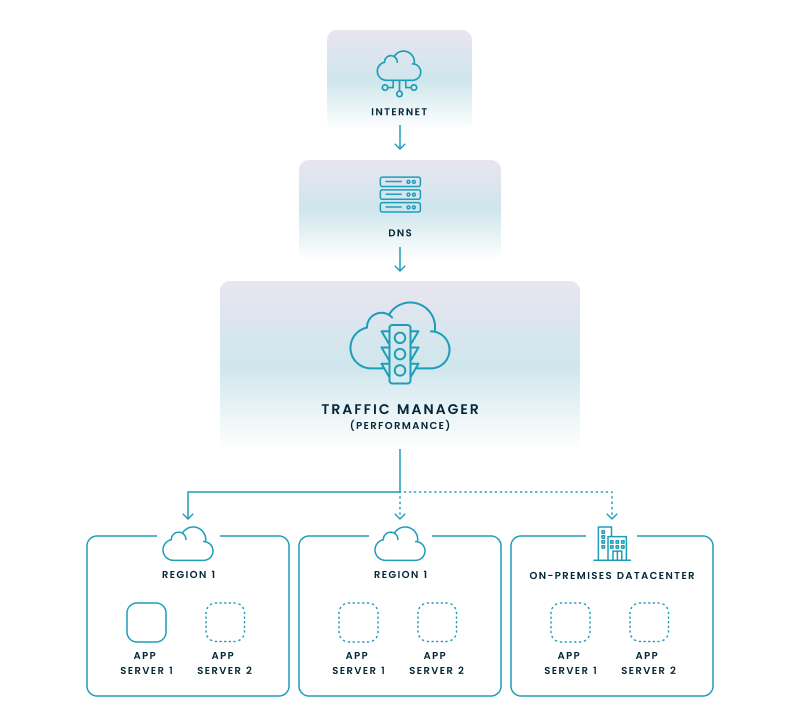
Traffic Manager is a DNS-based traffic management service that distributes traffic across Azure regions or on-premises datacenters. It's used for global application availability and disaster recovery.
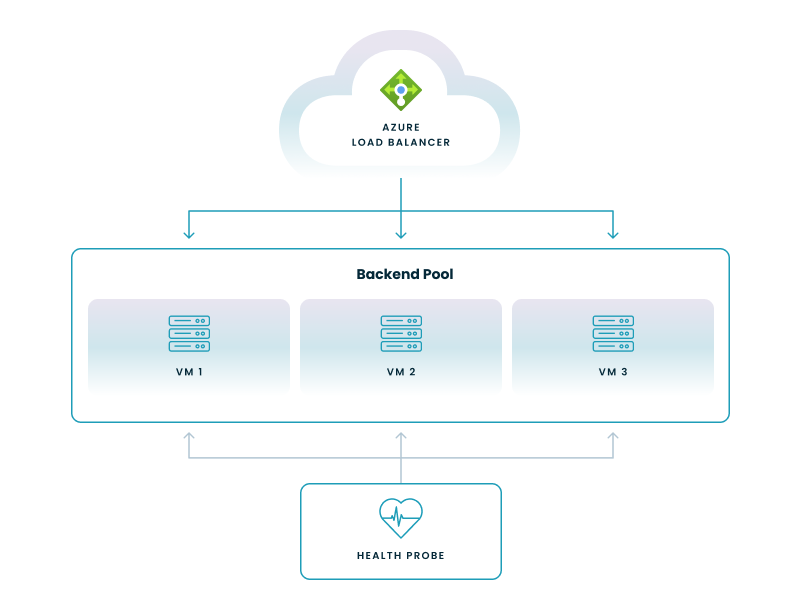
The backend pool contains the target resources (VMs, virtual machine scale sets, etc.) that receive traffic. The load balancer distributes traffic among these resources. In virtual desktop deployments, these backend VMs often run operating systems like Windows 11 Enterprise and utilize technologies like FSLogix for managing user profiles, with users connecting via protocols like RDP.
This defines how the load balancer receives traffic. For public load balancers, it's a public IP address. For internal load balancers, it's a private IP address within the VNet.
Health probes monitor the health of your backend resources. The load balancer only sends traffic to healthy resources.
Rules define how traffic is distributed to the backend pool.
NAT translates public IP addresses to the private IP addresses of your backend VMs. This allows your VMs to be accessible from the internet while remaining secure within your VNet.
Load Balancer automatically scales to handle increasing traffic demands. It can distribute traffic across a growing number of backend resources.
Load Balancer provides redundancy and failover capabilities.
NSGs and firewalls integrate with load balancers to secure your applications.
Azure Monitor allows you to track load balancer performance and health.
Azure Load Balancer offers two SKUs: Basic and Standard. Carefully consider your application's requirements for high availability, scalability, features, and budget.
This feature comparison table will help you compare:
| Feature | Basic Load Balancer | Standard Load Balancer |
|---|---|---|
| Global load balancing | No | Yes (with traffic manager) |
| Availability zones | No | Yes |
| Virtual machine scale sets | Limited support | Full support |
| Health probes | TCP, HTTP | TCP, HTTP, HTTPS |
| Session persistence | None | Configurable (IP Hash, Client IP, Client IP and Protocol) |
| Outbound connections | Provided via SNAT | Provided via SNAT and outbound rules |
| TCP/UDP protocols | Supported | Supported |
| Load balancing algorithms | Hash-based distribution | Hash-based distribution, least connections, etc. |
| Pricing | Lower | Higher |
| SLAs | No SLA | Yes |
Azure Load Balancer is a versatile tool. Here are some common use case scenarios:
Azure Load Balancer pricing is based on usage, including the number of load balancers deployed, the amount of data processed, and any associated features used. Key pricing factors include:
Pricing varies by region and SKU (Basic vs. Standard). The Standard Load Balancer generally has higher costs than the Basic Load Balancer due to its advanced features.
We recommended you consult the official Azure pricing page for the most up-to-date pricing details, as costs can change. The Azure pricing calculator can also help estimate costs based on your specific usage patterns.
You can manage load balancers through the Azure portal. The portal provides a user-friendly interface for creating, configuring, and monitoring your load balancers. Key tasks you can perform in the portal include:
Load Balancer seamlessly integrates with other Azure services to enhance your application architecture:
Both Azure and AWS offer load balancing services, but they have some key differences:
This comparison table will help you compare. It focuses on high-level concepts and avoids feature-by-feature parity:
| Feature | Azure Load Balancer | AWS Load Balancer |
|---|---|---|
| Types | Public, Internal, Application Gateway, Traffic Manager | Application Load Balancer, Network Load Balancer, Classic Load Balancer |
| Global LB | Traffic Manager | Global Accelerator, Route 53 Traffic Flow |
| Layer 7 LB | Application Gateway | Application Load Balancer |
| Layer 4 LB | Public/Internal Load Balancer | Network Load Balancer, Classic Load Balancer |
| Pricing | Based on usage (instance, data processed) | Based on usage (LCUs, data processed) |
| Integration | Integrates with other Azure services | Integrates with other AWS services |
Nerdio provides a management platform that helps you streamline the administration and optimization of your Azure infrastructure, including Azure Load Balancers. By integrating with your existing Azure services, Nerdio offers a centralized way to ensure your applications are highly available and scalable while also managing costs.
Managing Azure Load Balancers can be complex, especially in large-scale deployments. Nerdio simplifies this process by providing a unified interface for configuring and monitoring your load balancers. This includes:
One of the key challenges with cloud services is managing costs. Nerdio addresses this by using intelligent automation to ensure that your Azure resources, including those managed by a load balancer, are used efficiently.
For organizations using VDI, Azure Load Balancers are essential for distributing user traffic and ensuring a smooth, reliable experience. Nerdio enhances this by:
Discover how you can save up to 70% on Microsoft Azure costs by creating more efficient, secure, and reliable operations. Watch this demo.
See how you can optimize processes, improve security, increase reliability, and save up to 70% on Microsoft Azure costs.
Azure Load Balancer is a Microsoft Azure service that distributes network traffic across multiple backend resources, such as virtual machines or containers. This distribution improves application availability, scalability, and performance by preventing any single resource from being overwhelmed.
The Azure equivalent of AWS Elastic Load Balancing (ELB) is primarily the Azure Load Balancer service. While Application Gateway offers some overlapping functionality, Azure Load Balancer is the direct counterpart for general-purpose load balancing.
Azure Application Gateway is a specialized load balancer for web applications, operating at Layer 7 (application layer) and offering features like SSL offloading and WAF. Azure Load Balancer operates at Layer 4 (transport layer) and distributes traffic based on IP addresses and ports.
The purpose of a load balancer is to distribute incoming network traffic across multiple backend resources. This improves application availability, scalability, and performance by preventing overload and ensuring that requests are handled efficiently.
An Azure Load Balancer is a cloud-based service provided by Microsoft Azure that distributes network traffic across multiple resources, such as virtual machines or containers. It ensures high availability, scalability, and performance for applications running on Azure.
Monitoring load balancers allows you to track performance metrics, identify potential bottlenecks, and ensure the health and availability of your applications. Proactive monitoring helps prevent outages and optimize resource utilization.
Software product executive and Head of Product at Nerdio, with 15+ years leading engineering teams and 9+ years growing a successful software startup to 20+ employees. A 3x startup founder and angel investor, with deep expertise in Microsoft full stack development, cloud, and SaaS. Patent holder, Certified Scrum Master, and agile product leader.