NERDIO GUIDE

On-demand webinar
Beyond a conference — NerdioCon 2026: Learning, networking & unforgettable moments.
Save your spot
NERDIO GUIDE
Carisa Stringer | January 16, 2026
Standardization is the process of creating a repeatable, secure, and uniform configuration baseline across all client environments. For Managed Service Providers (MSPs), standardizing Microsoft 365 Business Premium is not just a technical preference; it is a business necessity for scaling profitably and maintaining a strong security posture.
By moving away from "bespoke" manual configurations toward a "manage-by-exception" model, MSPs can achieve an overall reduction in total support ticket volume by up to 45%. This consistency ensures every client meets enterprise-grade security standards like the CIS Benchmarks while allowing teams to focus on high-value strategy rather than repetitive admin tasks.
Standardization replaces unique, manual setups with a consistent framework that can be deployed rapidly across multiple tenants. This approach allows your engineering team to focus on high-value strategy rather than repetitive administrative tasks.
In a multi-tenant environment, standardization involves defining a "Golden Tenant" or a master template that contains your preferred security and productivity settings. Instead of logging into dozens of individual admin centers, you manage a single set of policies that are systematically pushed to all clients. This transition shifts your operations from reactive firefighting to a proactive, scalable model where every environment is inherently "secure by design."
Transitioning from "bespoke" management to a scalable practice requires a structural shift in how you deploy core services. The following Hub-and-Spoke architecture illustrates how a central orchestration layer allows you to push uniform identity, device, and security policies across your entire client portfolio simultaneously.
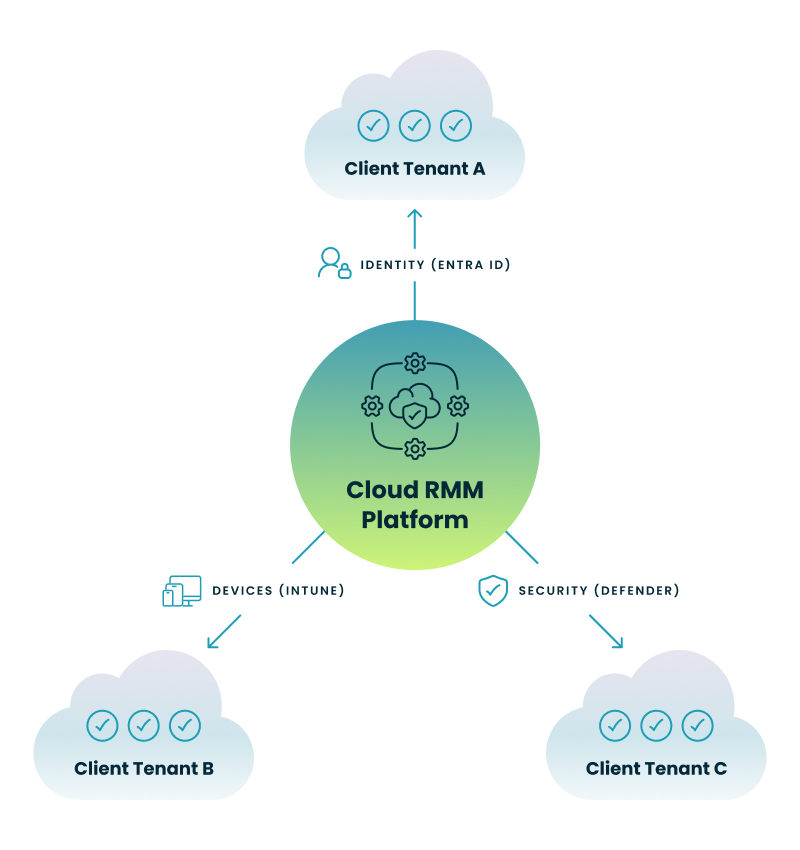
Managing multiple tenants manually leads to "portal fatigue" and significant labor costs, as technicians must navigate different interfaces for every minor change. Research indicates that organizations can achieve a 197% three-year return on investment with M365 when operational efficiency is maximized, but this ROI is often lost to manual repetition and human error (Gartner, 2025). Without a standard, you face "configuration drift," where client settings slowly deviate from your secure baseline, leading to unpredictable security gaps and longer troubleshooting times.
To help you evaluate the best path forward for your practice, the table below compares the three primary methods of managing tenant configurations—ranging from traditional manual entry to automated orchestration. This breakdown highlights how each approach impacts your team's technical overhead and overall ability to scale.
| Manual (Microsoft Portals) | Script-Based (PowerShell/Graph API) | Unified Orchestration (Nerdio) | |
|---|---|---|---|
| Onboarding Speed | Slow; manual entry per tenant. | Moderate; depends on script stability. | Fast; one-click baseline deployment. |
| Drift Detection | Manual audit; highly reactive. | Requires custom monitoring scripts. | Automated; continuous daily scans. |
| Technical Barrier | Low (but time-intensive). | High (requires DevOps/Scripting skills). | Moderate (GUI-driven automation). |
| Consistency | Low; high risk of human error. | High (until scripts break or age). | Total; enforced via global templates. |
| Maintenance | None (Microsoft manages portals). | High; must update scripts for API changes. | Low; Nerdio manages API updates. |
Standardization ensures that critical security features—such as Multi-Factor Authentication (MFA) and Conditional Access—are never overlooked during onboarding. By aligning your baseline with internationally recognized frameworks like the CIS Microsoft 365 Foundations Benchmark, you provide clients with a provable level of protection. This consistency is vital for meeting regulatory requirements and helps clients improve their overall cybersecurity posture, which can lead to lower cyber insurance premiums by demonstrating a hardened, audited environment.
Microsoft 365 Business Premium is a massive ecosystem, so standardization should focus on the "pillars" that offer the highest security and efficiency impact. Focusing on these core areas ensures you cover identity, devices, and data protection in one sweep.
Success in standardization depends on understanding which specific Microsoft 365 pillars offer the highest return on effort when automated. The following matrix identifies key settings within each pillar and the specific value that unified management brings to the deployment lifecycle.
| Standardization Pillar | Key Setting to Standardize | Common Scalability Challenge | Nerdio Automation Value |
|---|---|---|---|
| Identity (Entra ID) | Conditional Access & MFA | Replicating policies across 50+ tenants. | Global Solution Baselines push policies to all tenants at once. |
| Endpoints (Intune) | Compliance & Autopilot Profiles | Managing "portal fatigue" across tenants. | Unified Endpoint Management view for all devices in one console. |
| Security (Defender) | ASR Rules & EDR Settings | Ensuring settings don't "drift" over time. | Drift Management automatically alerts or reverts unauthorized changes. |
| Applications | Core App Stack (Office, etc.) | Keeping 3rd-party apps updated. | Unified App Management simplifies cross-tenant patching. |
Standardizing identity starts with Entra ID (formerly Azure AD) and the enforcement of Conditional Access policies. You should establish a standard set of policies that block legacy authentication, require MFA for all users, and implement geoblocking for high-risk regions. Standardizing these "gatekeeper" settings across all tenants reduces the risk of credential theft, which remains the primary vector for SMB breaches.
Using Microsoft Intune, included in Business Premium, allows you to push uniform Compliance Policies and Configuration Profiles to all endpoints. By standardizing Windows Autopilot profiles, you can achieve 'zero-touch' deployment to streamline the onboarding process, ensuring a new laptop is fully configured the moment a user signs in. To scale this further, MSPs can automate multi-tenant device lifecycle management to ensure every piece of hardware is tracked and secured from initial procurement through to retirement.
Microsoft Defender for Business provides enterprise-grade protection that should be configured identically across your client base. This includes standardizing Attack Surface Reduction (ASR) rules, automated investigation and remediation (AIR) levels, and endpoint detection and response (EDR) settings. Tools like Nerdio allow you to package these Defender settings into solution baselines, ensuring that no client is left with "default" settings that might be too permissive.
Building a baseline requires a structured approach that moves from documentation to automation. This process ensures that your "Gold Standard" is both technically sound and easy to replicate.
Even with a solid plan, the reality of diverse client needs can create friction. Understanding these hurdles early allows you to build a more resilient management practice.
The most common challenge is the "one-size-fits-most" problem, where a specific client requires an exception to your global security rule (e.g., an older app that doesn't support MFA). A mature standardization strategy uses a "Manage by Exception" approach: apply the global baseline to 95% of the environment and document the 5% deviation. As shown in the comparison table in the first section, moving to a unified orchestration model allows these exceptions to be managed centrally rather than documented in siloed spreadsheets. When evaluating alternatives to M365 multi-tenant management tools, this ability to handle granular exceptions while maintaining global compliance is a critical differentiator.
This remains true even when using structured frameworks like CyberDrain CIPP, as maintaining the underlying scripts for compliance often becomes a full-time job. This "maintenance tax" often eats into the efficiency gains of automation, leading many MSPs to shift toward purpose-built orchestration platforms that handle the API updates and script maintenance for them.
Nerdio Manager for MSP is designed specifically to eliminate the manual overhead of multi-tenant management. It acts as a unified orchestration layer that sits on top of Microsoft 365, turning complex manual tasks into automated, repeatable workflows. This orchestration extends capabilities significantly, allowing MSPs to even automate multi-tenant AVD image lifecycle management alongside their standard M365 policies.
Nerdio provides Solution Baseline Templates that allow you to define your "Gold Standard" configurations for Entra ID, Intune, and Defender in one place. With a few clicks, you can push these templates to all your managed tenants simultaneously. This ensures that every new client you onboard is immediately aligned with your best practices, reducing onboarding time by as much as 60% (AvePoint, 2025).
One of Nerdio’s most powerful features is its Drift Management capability. The platform continuously monitors client tenants against your assigned baselines; if a setting is changed—whether accidentally or maliciously—Nerdio alerts your team or can even be configured to automatically "re-apply" the correct setting. This ensures your clients stay secure without requiring manual audits.
Configuration drift is an inevitable challenge in dynamic cloud environments, where even minor unauthorized changes can compromise security. The following diagram illustrates how Nerdio automates the lifecycle of maintaining a "Golden Tenant" state through a continuous loop of monitoring and remediation.
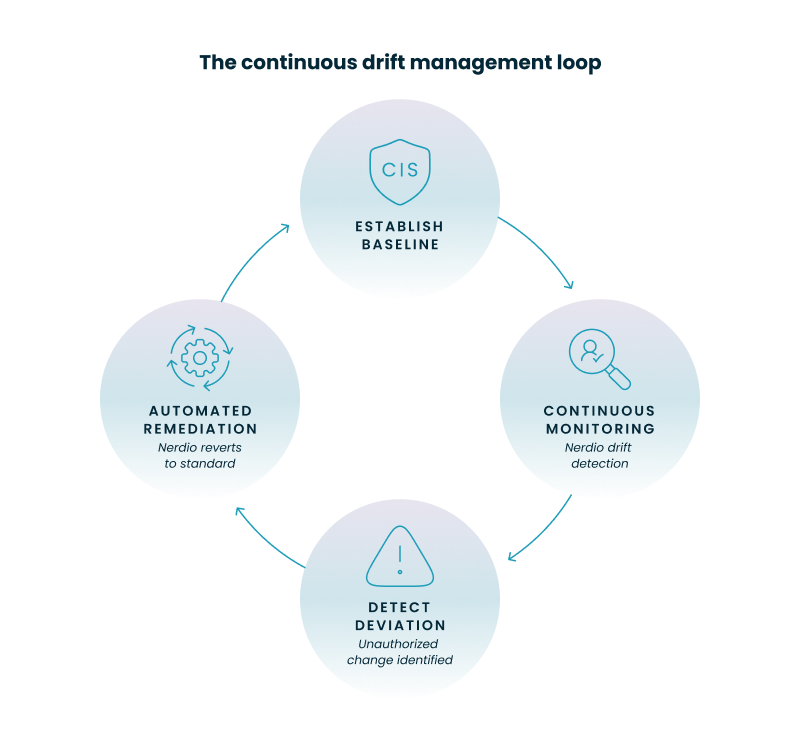
To maintain a hardened security posture at scale, Nerdio orchestrates the following four stages of the drift management lifecycle:
Instead of "portal hopping" between dozens of Microsoft admin centers, Nerdio provides a single pane of glass for all tenants. This unified console allows technicians to manage users, licenses, and Intune policies across the entire client base from one interface. By utilizing Nerdio's Role-Based Access Control (RBAC), you can also empower Level 1 technicians to perform complex tasks (like device wipes or password resets) securely, without granting them full Global Admin rights in the Microsoft portal. This consolidation is a key feature of robust multi-tenant management tools for Microsoft 365, enabling technicians to oversee vast environments without switching contexts.
Beyond technical consistency, the primary driver for automation is the recovery of billable engineering time. While the individual tasks outlined in the table below show massive performance gains—often exceeding 90% per action—it is the cumulative effect of these efficiencies across your entire client base that drives a sustainable, overall reduction in total support ticket volume by up to 45%. This comparison demonstrates the quantifiable efficiency gains realized for individual management tasks when moving from manual multi-tenant management to an automated framework.
| Manual Estimated Time | Nerdio Automated Time | Efficiency Gain | |
|---|---|---|---|
| New Tenant Onboarding | 4 - 8 Hours | < 30 Minutes | ~90% Redux |
| Security Policy Audit | 1 Hour per Tenant | < 5 Minutes (Global View) | ~95% Redux |
| Remediating Drift | 1 - 2 Hours per Incident | Instant (Auto-remediation) | 100% Redux |
| Password/MFA Reset | 10 - 15 Minutes | 2 Minutes (via RBAC) | ~80% Redux |
This Nerdio for Microsoft 365 overview explains how the platform optimizes Business Premium features like Intune and Defender to bridge talent gaps and enhance service delivery.
Microsoft 365 Business Premium is an integrated solution designed for small to medium-sized businesses that combines best-in-class productivity tools with advanced security and device management capabilities. It includes the full suite of Office applications along with enterprise-grade security products such as Microsoft Defender for Business, Microsoft Intune, and Microsoft Entra ID Premium P1. The package is tailored for organizations with up to 300 users, offering sophisticated protection against phishing, ransomware, and other evolving cyber threats.
MSPs should leverage Business Premium to deliver comprehensive, "wrap-around" security services from a single license, which reduces the complexity of managing multiple third-party tools. Standardizing on this SKU allows partners to drive business growth through recurring revenue while demonstrating clear ROI to clients via tools like Microsoft Secure Score. Additionally, it enhances operational efficiency and client retention by providing a consistent, highly secure baseline that adapts to modern workforce needs.
IT automations for Business Premium include the use of Microsoft Autopilot and Intune to enable "zero-touch" device provisioning and uniform policy enforcement across managed endpoints. MSPs also utilize PowerShell scripts and specialized orchestration platforms to automate bulk license assignments and the deployment of standardized security baselines. Furthermore, AI-driven tools like Microsoft Copilot and Power Automate are used to streamline repetitive business processes such as data entry, approvals, and threat remediation.
MSPs standardize deployment by defining a "Golden Tenant" or master template that contains preferred security, identity, and compliance policies. This template is then pushed across client environments using centralized management platforms or automated deployment guides to ensure every tenant starts with the same best practices. This hub-and-spoke architecture allows for multi-tenant orchestration of settings like Conditional Access and Defender rules, significantly reducing manual configuration errors and "portal fatigue".

On-demand webinar

Carisa Stringer
Head of Product Marketing
Carisa Stringer is the Head of Product Marketing at Nerdio, where she leads the strategy and execution of go-to-market plans for the company’s enterprise and managed service provider solutions. She joined Nerdio in 2025, bringing 20+ years of experience in end user computing, desktops-as-a-service, and Microsoft technologies. Prior to her current role, Carisa held key product marketing positions at Citrix and Anthology, where she contributed to innovative go-to-market initiatives. Her career reflects a strong track record in driving growth and adoption in the enterprise technology sector. Carisa holds a Bachelor of Science in Industrial Engineering from the Georgia Institute of Technology.