Remote Desktop Protocol (RDP)
This enterprise guide to Remote Desktop Protocol (RDP) provides concise insights into core concepts, security, deployment choices, costs, and future trends.
Beyond a conference — NerdioCon 2026: Learning, networking & unforgettable moments.
Save your spot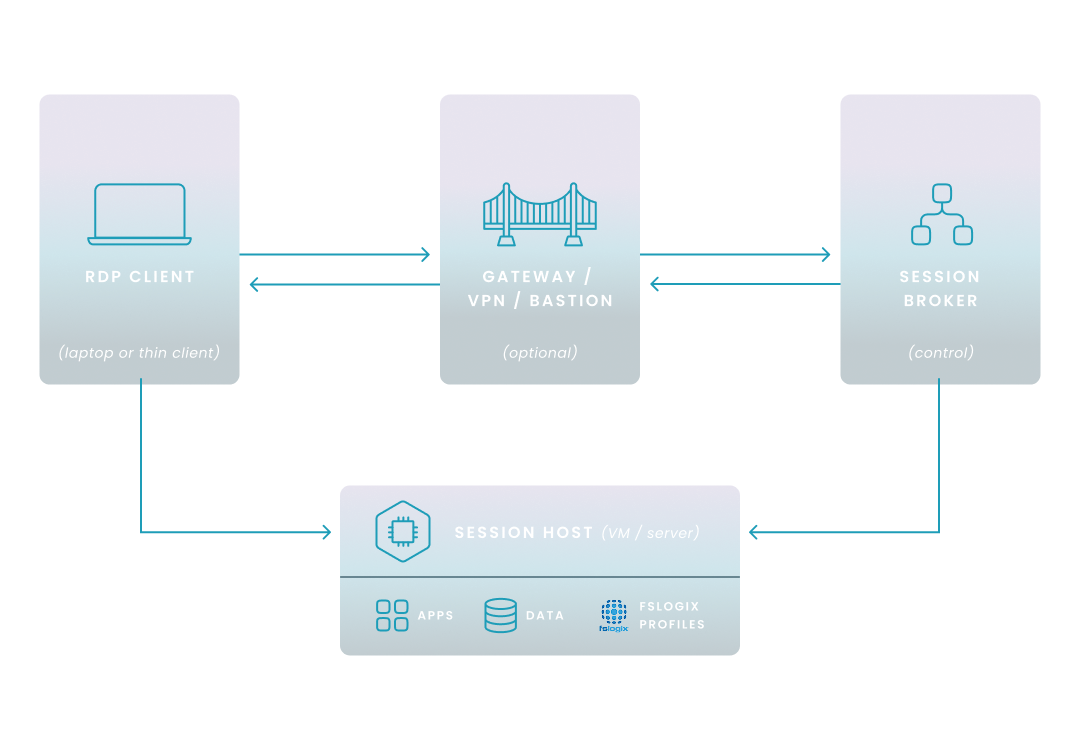
This enterprise guide to Remote Desktop Protocol (RDP) provides concise insights into core concepts, security, deployment choices, costs, and future trends.
Carisa Stringer | June 25, 2025
Microsoft’s Remote Desktop Protocol (RDP) is a Windows-native standard that streams your keyboard, mouse, and display data over TCP/UDP 3389, letting you operate a remote PC or server as if you were on-site.
Embedded in Azure Virtual Desktop and Windows 365, RDP powers routine administration, service-desk fixes, and secure work-from-anywhere sessions. Traffic is wrapped in TLS and can enforce Network Level Authentication, while virtual channels redirect printers, clipboards, and USB devices to keep workflows intact.
By decoupling the user experience from the physical machine, RDP helps you centralize management, cut travel, and maintain business continuity—provided you lock it down with strong credentials, MFA, and tightly scoped network access.
You want a clear view of how RDP may help—or hinder—your organization before you green-light another remote-access project. The quick lists below surface the upside RDP functionalities (centralized control, productivity, cost) and the trade-offs (security exposure, performance, licensing) that matter most at the executive level.
Remote Desktop Protocol is a cornerstone of Virtual Desktop Infrastructure (VDI), which is the practice of hosting desktop operating systems on a central server and delivering them to users on demand, thereby offering businesses enhanced data control, streamlined endpoint management, and flexible remote access capabilities.
Ultimately, technologies like RDP and VDI are pivotal in shaping an organization's End User Computing (EUC) strategy, which focuses on delivering seamless and secure access to applications and data for employees, regardless of their device or location, to enhance productivity and business agility.
RDP is a prime target for ransomware crews and credential-stuffing bots, so “working out of the box” is never enough. A layered defense—hardening first, then monitoring, then rapid response—cuts vulnerability without killing usability.
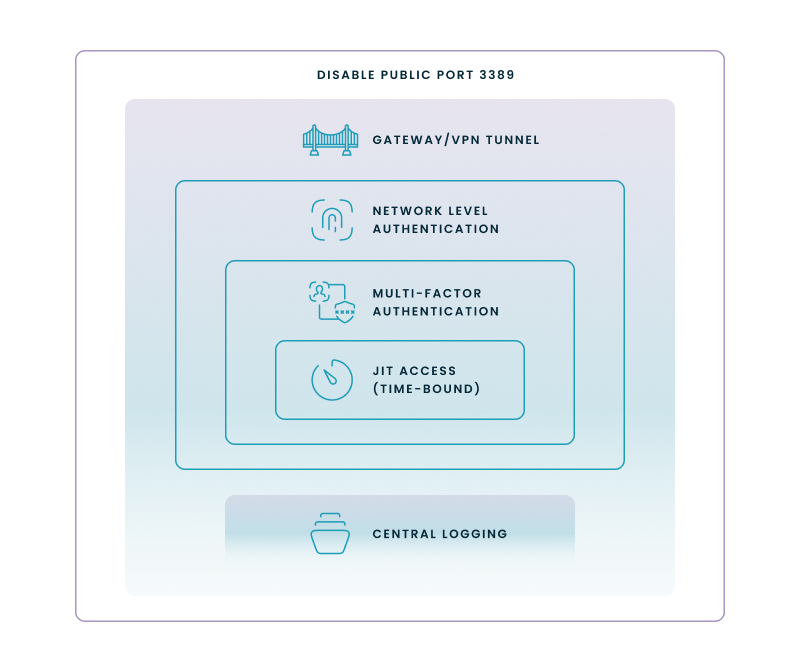
Reading inward (outer ring → core) on the image above:
| Control | What to Log | Where to Send It | Why It Matters |
|---|---|---|---|
| Windows Event IDs 4624/4625, 1149 | Successful / failed logons, RemoteDesktopServices-RDPCore events | SIEM (Sentinel, Splunk, etc.) | Spot brute-force bursts and orphaned accounts |
| RD Gateway logs | Connection authorization policy hits | Central syslog | Prove MFA and client health checks |
| Azure Monitor / Log Analytics | Heartbeat + SecurityBaseline | Azure Sentinel | Real-time anomaly alerts |
Add weekly review of lockout counts and privilege changes; CISA recommends central log retention for at least 12 months.
Action tip: Pair continuous threat-intel feeds with SIEM rules that trigger on repeated 3389 scans, spikes in 4625 failures, or off-hours logons from new geos.
These controls, applied together, harden RDP without derailing the workflows it enables—keeping your admins productive and your board off the breach-notification headlines.
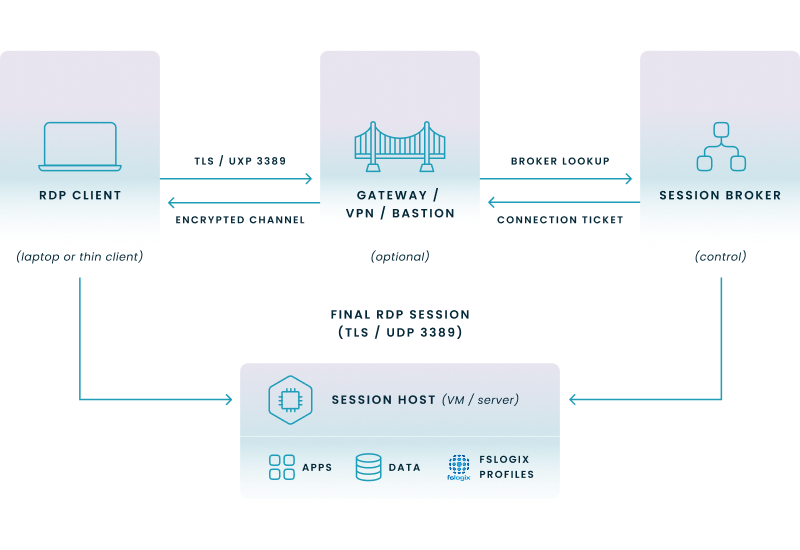
Key callouts for the diagram above:
When considering remote desktop solutions, many businesses evaluate options like AVD and Windows 365, which serve as compelling Citrix DaaS alternatives, particularly for organizations seeking deep integration with Microsoft Azure services and modern Desktop as a Service (DaaS) capabilities.
No single RDP setup fits every organization. Your options range from a classic on-prem Remote Desktop Services (RDS) farm of RDP servers to fully managed cloud desktops. The matrix below helps you map each model to security, scalability, and licensing needs.
For businesses exploring virtual desktop solutions, Azure VDI represents the capability to host and manage these desktops on Microsoft's cloud platform, with Azure Virtual Desktop (AVD) being a key service that provides global scalability, centralized management, and access to Windows desktops from virtually anywhere.
| Connectivity Option | Best For | Key Pros | Key Cons |
|---|---|---|---|
| RD Gateway | Contractors & quick roll-outs | HTTPS tunnelling (443), granular CAP/RAP policies | Still exposes a public endpoint; adds extra hop |
| Site-to-Site or User VPN | Full-network access, small user counts | No extra RDS role; encrypts all traffic | Backhauls Internet traffic unless split-tunnel; higher latency for chatty apps |
| Azure Private Link | Strict zero-trust or regulated workloads in AVD | Keeps traffic on Microsoft backbone; no inbound public IP | Azure-only; requires DNS & VNet plumbing |
RD Gateway suits remote help-desk scenarios where you need to avoid VPN sprawl, while a VPN is simpler when users already need broad network access. Private Link is the go-to when auditors demand that RDP never traverse the Internet.
| Model | License Components | Typical Cost Pattern | Notes |
|---|---|---|---|
| On-prem RDS | Windows Server OS + RDS CALs (Per User or Per Device) | One-time CAL purchase, plus server hardware/VMs | CALs must match or exceed operating systems version. |
| Azure Virtual Desktop | Eligible Microsoft 365 or Windows E3/E5 per-user License (includes Windows VDA rights) + Azure compute/storage | Opex: pay-as-you-go VM hours; shut down hosts to save | No extra RDS CALs for internal users. |
| Windows 365 Cloud PC | Per-user subscription that bundles License + compute (e.g., 4 vCPU/16 GB RAM at US $101/user/mo). | Flat monthly fee; no surprise VM charges | Ideal for predictable headcount. |
License tip: If you own Microsoft 365 E3/E5, you already have the user rights to access AVD session hosts; you still pay Azure VM runtime but skip extra CALs.
These deployment choices let you balance control, security, and cost. Start with the regulatory or latency constraint that matters most, then pick the model—and License mix—that aligns with it.
A smooth RDP session hinges on three things you can control: network quality, protocol settings, and host resources. Tune each layer and your remote workforce sees near-local responsiveness—even across continents.
Bandwidth cheat-sheet (single 1920 × 1080 monitor)
| Activity | Default Mode | H.264/AVC 444 |
|---|---|---|
| Idle screen | 0.3 Kbps | 0.3 Kbps |
| Word editing | 100–150 Kbps | 200–300 Kbps |
| Excel with charts | 150–200 Kbps | 400–500 Kbps |
Combine UDP transport, smart codec choices, and disciplined monitoring to give distributed teams an experience close to local desktops—without overspending on bandwidth or hardware.
Regulators treat remote access as a high-risk activity, so you must map RDP settings to formal controls—not just “best effort” hardening. The table below shows how common frameworks call out remote-desktop security and the concrete actions you can prove during an audit.
TABLE
By tying each RDP control to a specific framework requirement, you give auditors clear evidence while ensuring your remote-desktop footprint meets the same bar as the rest of your security program.
| Framework | Relevant Control(s) | What the Control Asks For | How You Satisfy It with RDP |
|---|---|---|---|
| NIST SP 800-53 Rev. 5 | AC-17 Remote Access, AU-2 Audit Events | Authorize, encrypt, and monitor every remote session. | Remove public 3389, force TLS 1.2+, enable Network Level Auth, forward Event IDs 4624/4625/1149 to SIEM. |
| ISO 27001:2022 | Annex A 6.7 Remote Working | Define and enforce a remote-access policy with technical controls. | Document RDP hardening in your ISMS; run annual policy attestation and access recertification. |
| PCI DSS v4.0 | Req. 2.2.6, 8.3 MFA, 10.2 Log Review | Secure remote admin to the CDE with MFA, jump hosts, and central logging. | Route RDP through RD Gateway with MFA; review logs daily for unauthorized access. |
| HIPAA Security Rule | 45 CFR §164.312(a)(2)(iv) Encryption, 164.312(b) Audit Controls | Protect ePHI in transit and record remote activity. | Enforce TLS, disable clipboard redirection for PHI apps, retain logs ≥6 years. |
By tying each RDP control to a specific framework requirement, you give auditors clear evidence while ensuring your remote-desktop footprint meets the same bar as the rest of your security program.
Join us for a webinar to discover how to take Windows to the cloud. Get insights from industry leaders on navigating the modern workspace and driving secure, cloud-powered operations.
Business impact, not technical elegance, decides whether an RDP rollout succeeds. Use the checklist below in board or steering-committee sessions to surface the cost, risk, and change-management issues that commonly derail projects after launch.
| Executive Question | Why It Matters | Data Points / Proof to Gather |
|---|---|---|
| What is our total cost of ownership across licensing and infrastructure? | CALs, cloud compute, gateways, and support contracts can outweigh the “built-in” appeal of RDP. | RDS User CAL ≈ US $220 one-time; Windows 365 Cloud PC 4 vCPU/16 GB = US $101 user/mo; AVD adds Azure VM runtime + storage |
| How will we mitigate the 84% breach statistic tied to RDP abuse? | RDP was leveraged in 84% of 2024 incident-response cases — attackers prefer it because valid logons slip past AV. | Require MFA, NLA, and no public 3389; budget for SIEM tuning and penetration tests. |
| Can the chosen model scale up—or down—within target SLAs? | Holiday peaks or M&A events strain session hosts. | AVD autoscaling shuts down idle VMs; on-prem farms may need extra hardware. |
| What user-experience targets (latency, frame rate) will we guarantee? | Poor UX drives shadow IT and support tickets. | Aim for <100 ms RTT and UDP Shortpath; pilot with high-pixel-density users first. |
| Which compliance clauses govern remote desktop in our industry? | Auditors will ask for explicit mapping of NIST AC-17, ISO 27001 A 6.7, PCI DSS 4.0 Req 8.3, etc. | Maintain policy docs + 12 months of RDP logs. |
| What is our exit or migration strategy? | Vendor-lock can trap you in legacy CALs or region-specific cloud images. | Capture image portability requirements and CAL buy-back terms in contracts. |
| How will we recover if an RDP gateway is compromised? | Gateway is a single point of failure (and breach). | Plan segmented management networks, JIT admin, and scripted rebuilds. |
| Do we have the skills and monitoring budget to operate this 24/7? | RDP misuse indicators often surface after hours. | Factor in SOC coverage or MDR subscription that watches 4625/1149 spikes. |
Work through these questions early, document the evidence, and you’ll approve—or reject—an RDP initiative with eyes wide open, not on gut feel.
Nerdio Manager sits on top of Azure and Windows 365, automating the pieces you would otherwise script by hand. The platform’s GUI, policies, and auto-scaling engine help you roll out thousands of cloud desktops fast—and keep the monthly bill under control.
Click-through provisioning. Deploy session-host images, FSLogix profiles, and AVD host pools from a single wizard instead of multiple Azure blades. Penn State’s IT team highlighted the “ease and speed of implementation.”
Graphical runbooks. Schedule patching, reboots, image swaps, and scripted actions without PowerShell.
Bulk actions. Start, stop, or resize hundreds of VMs at once—useful during academic breaks or seasonal demand spikes.
| Metric | Typical Azure Baseline | With Nerdio Auto-scaling |
|---|---|---|
| Compute/storage savings | — | 50–75% average |
| Real-world case | Kaplan’s AVD rollout | 71% reduction; supports 1,000+ users |
Key levers include schedule-based “burst” scaling, idle-host hibernation, and right-sizing based on actual CPU/RAM use.
Azure AD integration. Delegate management rights by subscription, resource group, or host pool; auditors see least-privilege assignments in one pane.
Policy workflow. Push Intune baselines, conditional-access rules, and RBAC updates together—reducing drift across hundreds of desktops.
Central logging. Nerdio pipes activity to Azure Monitor or your SIEM for PCI/NIST evidence.
Unified console. The same interface governs AVD session hosts, Cloud PCs, and Intune device policies.
AI-powered cost and usage recommendations. Version 7 surfaces License and VM rightsizing tips so you can act before budgets overrun.
By automating host management, shrinking compute waste, and wrapping everything in delegated policy controls, Nerdio lets you deliver enterprise-scale RDP and AVD environments without a proportional jump in headcount or spend.
See this demo to discover how you can simplify operations, enhance security, and lower the total Azure cost of your entire Windows 365 or AVD environment with Nerdio Manager.
See how you can optimize processes, improve security, increase reliability, and save up to 70% on Microsoft Azure costs.
Remote Desktop Protocol (RDP) is Microsoft’s own application-layer protocol for interactive graphics remoting; it encapsulates session traffic in TCP—and, in modern releases, optionally in UDP—by default on port 3389.
RDP listens simultaneously on TCP 3389 and UDP 3389; the client and host negotiate which transport to use, falling back to TCP if UDP is blocked.
Remote Desktop Services (RDS) is the Windows server role that delivers multi-session desktops and apps; it relies on the RDP protocol for graphics and device redirection, supplemented by support services such as RD Gateway (HTTPS) and RD Web (HTTP/HTTPS).
VPNs and RDP solve different problems: a VPN creates an encrypted tunnel to your network, while RDP provides the remote desktop once inside. CISA advises never exposing RDP directly to the Internet—instead, place it behind a VPN or RD Gateway and enforce MFA—so the safest design is “VPN + RDP,” not one replacing the other.
RDP supports TLS encryption and Network Level Authentication, so—when you add strong passwords, MFA, and restricted network access—it can meet enterprise security requirements. However, publicly open RDP ports remain a top ransomware entry point, so hardening and continuous monitoring are mandatory to keep it safe.


Carisa Stringer
Head of Product Marketing
Carisa Stringer is the Head of Product Marketing at Nerdio, where she leads the strategy and execution of go-to-market plans for the company’s enterprise and managed service provider solutions. She joined Nerdio in 2025, bringing 20+ years of experience in end user computing, desktops-as-a-service, and Microsoft technologies. Prior to her current role, Carisa held key product marketing positions at Citrix and Anthology, where she contributed to innovative go-to-market initiatives. Her career reflects a strong track record in driving growth and adoption in the enterprise technology sector. Carisa holds a Bachelor of Science in Industrial Engineering from the Georgia Institute of Technology.